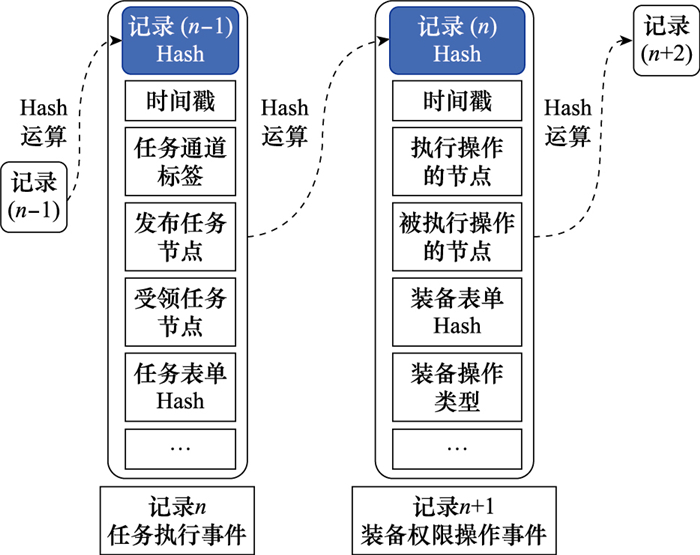
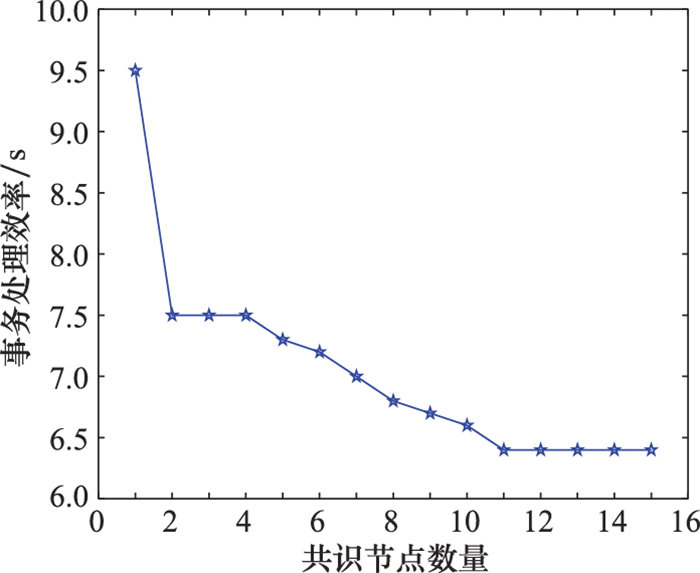
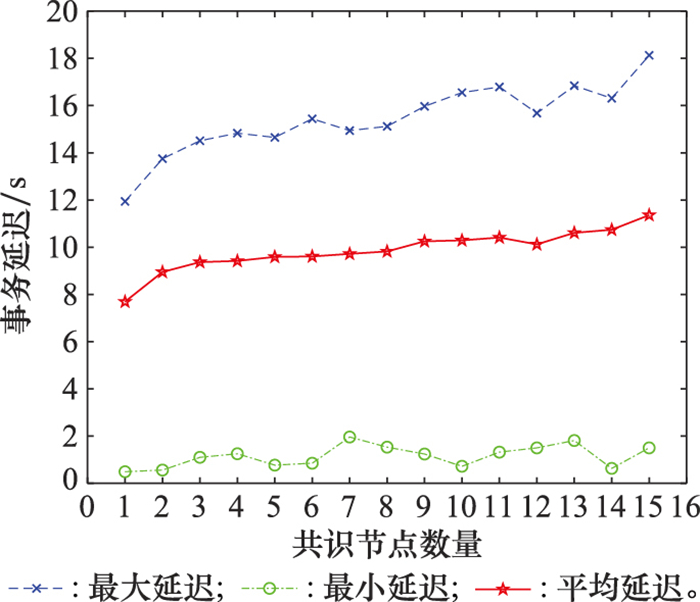
Systems Engineering and Electronics ›› 2022, Vol. 44 ›› Issue (9): 2817-2825.doi: 10.12305/j.issn.1001-506X.2022.09.15
• Systems Engineering • Previous Articles Next Articles
Blockchain based method of dynamic command and control
Yongqi PAN1,2, Wei WEI1,*, Yi LIU2, Cheng ZHU2
- 1. College of Information and Communication, National University of Defense Technology, Wuhan 430000, China
2. Science and Technology on Information Systems Engineering Laboratory, National University of Defense Technology, Changsha 410000, China
-
Received:2021-06-21Online:2022-09-01Published:2022-09-09 -
Contact:Wei WEI
CLC Number:
Cite this article
Yongqi PAN, Wei WEI, Yi LIU, Cheng ZHU. Blockchain based method of dynamic command and control[J]. Systems Engineering and Electronics, 2022, 44(9): 2817-2825.
share this article
| 1 | ALBERTS D S , HAYES R E . Power to the edge: command control in the information age[M]. Washington, DC: CCRP Publication Series, 2003. |
| 2 | ALBERTS D S, BERNIER F, CHAN K, et al. C2 in underdeveloped, degraded and denied operational environments[C]//Proc. of the International Command & Control Research Symposium, 2013. |
| 3 | TRAN H T, DOMERANT J C, MAVRIS D N. A system-of-systems approach for assessing the resilience of reconfigurable command and control networks[C]//Proc. of the AIAA SciTech Forum, 2015. |
| 4 |
ZHU Y , ZHANG X , JU Z Y , et al. A study of blockchain technology development and military application prospects[J]. Journal of Physics: Conference Series, 2020, 1507 (5): 052018.
doi: 10.1088/1742-6596/1507/5/052018 |
| 5 | RAJA W A , HAYA H , IBRAR Y , et al. Blockchain for aerospace and defense: opportunities and open research challenges[J]. Computers & Industrial Engineering, 2021, 151, 106982. |
| 6 | RAHAYU S B, JUSOH N, HALIP M H M, et al. A conceptual model of military blockchain for repair parts supply chain management[C]//Proc. of the International Conference on Computer & Information Sciences, 2021: 146-150. |
| 7 | SIMERLY M T , KEENAGHAN D J . Blockchain for military logistics[J]. Army Sustainment, 2019, 51 (4): 48- 49. |
| 8 | BILYANA L , SALE L . Weaponising blockchain: military applications of blockchain technology in the US, China and Russia[J]. Royal United Services Institution, 2021, 166 (3): 46- 56. |
| 9 | GOLAM M, LEE J M, KIM D S. A UAV-assisted blockchain based secure device-to-device communication in internet of military things[C]//Proc. of the International Conference on Information and Communication Technology Convergence, 2020: 1896-1898. |
| 10 | WU Y, DAI H N, WANG H, et al. Blockchain-based privacy preservation for 5G-enabled drone communications[C]//Proc. of the IEEE Network, 2021: 50-56. |
| 11 | AKTER R, BHARDWAJ S, LEE J M, et al. Highly secured C3I communication network based on blockchain technology for military system[C]//Proc. of the International Conference on Information and Communication Technology Convergence, 2019: 780-783. |
| 12 | GHIMIRE B, RAWAT D B, LIU C, et al. Sharding-enabled blockchain for software-defined internet of unmanned vehicles in the battlefield[C]//Proc. of the IEEE Network, 2021: 101-107. |
| 13 |
赵国宏. 军事区块链研究[J]. 指挥与控制学报, 2019, 5 (4): 259- 268.
doi: 10.3969/j.issn.2096-0204.2019.04.0259 |
|
ZHAO G H . Military blockchain research[J]. Journal of Command and Control, 2019, 5 (4): 259- 268.
doi: 10.3969/j.issn.2096-0204.2019.04.0259 |
|
| 14 |
王飞跃, 袁勇, 王帅, 等. 军事区块链: 从不对称的战争到对称的和平[J]. 指挥与控制学报, 2018, 4 (3): 175- 182.
doi: 10.3969/j.issn.2096-0204.2018.03.0175 |
|
WANG F Y , YUAN Y , WANG S , et al. Military blockchain: from asymmetric war to symmetrical peace[J]. Journal of Command and Control, 2018, 4 (3): 175- 182.
doi: 10.3969/j.issn.2096-0204.2018.03.0175 |
|
| 15 | 刘毅, 朱承, 成清. 面向敏捷指控的区块链赋能跨域服务架构[J]. 指挥与控制学报, 2020, 8 (2): 169- 178. |
| LIU Y , ZHU C , CHENG Q . Blockchain empowered cross-domain service architecture for agile command and control[J]. Journal of Command and Control, 2020, 8 (2): 169- 178. | |
| 16 |
刘瑞, 马玉皓, 祁志民. 面向未来陆战场作战的区块链技术军事应用构想[J]. 火力与指挥控制, 2020, 45 (11): 16- 21.
doi: 10.3969/j.issn.1002-0640.2020.11.004 |
|
LIU R , MA Y H , QI Z M . Conception of military application of block chain technology for future land battlefield operations[J]. Fire and Command and Control, 2020, 45 (11): 16- 21.
doi: 10.3969/j.issn.1002-0640.2020.11.004 |
|
| 17 | 杜行舟, 张凯, 江坤, 等. 基于区块链的数字化指挥控制系统信息传输与追溯模式研究[J]. 计算机科学, 2018, 45 (S2): 576- 579. |
| DU X Z , ZHANG K , JIANG K , et al. Research on information transmission and traceability mode of digital command and control system based on blockchain[J]. Computer Science, 2018, 45 (S2): 576- 579. | |
| 18 |
巫岱玥, 余祥, 王超, 等. 基于区块链的信息系统数据保护技术研究[J]. 指挥与控制学报, 2018, 4 (3): 183- 188.
doi: 10.3969/j.issn.2096-0204.2018.03.0183 |
|
WU D Y , YU X , WANG C , et al. Research on data protection technology of information system based on blockchain[J]. Journal of Command and Control, 2018, 4 (3): 183- 188.
doi: 10.3969/j.issn.2096-0204.2018.03.0183 |
|
| 19 |
舒展翔, 李腾飞, 余祥. 基于区块链的指挥信息系统用户权限管理问题研究[J]. 指挥与控制学报, 2019, 5 (2): 107- 114.
doi: 10.3969/j.issn.2096-0204.2019.02.0107 |
|
SHU Z X , LI T F , YU X . Research on user permission management of command information system based on blockchain[J]. Journal of Command and Control, 2019, 5 (2): 107- 114.
doi: 10.3969/j.issn.2096-0204.2019.02.0107 |
|
| 20 | WRONA K, JAROSZ M. Use of blockchains for secure binding of metadata in military applications of IoT[C]//Proc. of the IEEE 5th World Forum on Internet of Things, 2019: 213-218. |
| 21 |
TEJASVI A A , VINAY C A , NISHAD S A , et al. Applications of blockchain in unmanned aerial vehicles: a review[J]. Vehicular Communications, 2020, 23, 100249.
doi: 10.1016/j.vehcom.2020.100249 |
| 22 | ALBERTS D S , GARSTKA S . Network centric warfare: developing and leveraging information superiority[M]. Washington DC: CCRP Publication Series, 1999. |
| 23 |
LEVCHUK G M , LEVCHUK Y N , LUO J . Normative design of organizations-partⅡ: organizational structure[J]. IEEE Trans.on Systems, Man, and Cybernetics-Part A: Systems and Humans, 2002, 32 (3): 360- 375.
doi: 10.1109/TSMCA.2002.802820 |
| 24 | BALLARD J J . The proper application of nominative fair use in trademark law: why international information systems security certification consortium, Inc. v. Security University, LLC sets the preeminent standard[J]. Loyola of Los Angeles Law Review, 2018, 51, 523. |
| 25 |
尹荣荣, 张文元, 杨绸绸, 等. 基于简化云与K/N投票的选择性转发攻击检测方法[J]. 电子与信息学报, 2020, 42 (12): 2841- 2848.
doi: 10.11999/JEIT190274 |
|
YIN R R , ZHANG W Y , YANG C C , et al. A selective forwarding attack detection method based on simplified cloud and K/N voting model[J]. Journal of Electronics & Information Technology, 2020, 42 (12): 2841- 2848.
doi: 10.11999/JEIT190274 |
|
| 26 | HORS A J L, KUHRT T. Smart contracts and chaincode[EB/OL]. [2021-06-11]. https://hyperledger-fabric.readthedocs.io/en/release-2.2/smartcontract/smartcontract.html#channels. |
| 27 |
AGRAWAL P , TARCA A , WOODLIFF D . External auditors' evaluation of a management's expert's credibility: evidence from Australia[J]. International Journal of Auditing, 2020, 24 (1): 90- 109.
doi: 10.1111/ijau.12181 |
| 28 |
PITT R , WYBORN C , PAGE G , et al. Wrestling with the complexity of evaluation for organizations at the boundary of science, policy, and practice[J]. Conservation Biology, 2018, 32 (5): 998- 1006.
doi: 10.1111/cobi.13118 |
| 29 | ZAKIROVA Y, LATYPOVA M, GAFUROVA S. The concept of creating a form-based code of Zelenodolsk[C]//Proc. of the E3S Web of Conferences EDP Sciences, 2021, 274: 01021. |
| 30 | PAN Y, LIU Y, ZHU C. Secure personal unmanned aerial vehicle lease scheme based on blockchain[C]//Proc. of the IEEE 14th International Conference on Anti-counterfeiting, Security, and Identification, 2020: 197-203. |
| 31 | ANDROULAKI E, BARGER A, BORTNIKOV V. Hyperledger fabric: a distributed operating system for permissioned blockchains[C]//Proc. of the 13th EuroSys Conference, 2018. |
| 32 | International Business Machines Corporation. Hyperledger caliper[EB/OL]. [2021-06-11]. https://hyperledger.github.io/caliper/. |
| 33 | DREYER J, FISCHER M, TONJES R. Performance analysis of hyperledger fabric 2.0 blockchain platform[C]//Proc. of the Workshop on Cloud Continuum Services for Smart IoT Systems, 2020: 32-38. |
| [1] | Lisha CHEN, Xuelian LI, Juntao GAO. Accountable data trading scheme supporting data integrity verification [J]. Systems Engineering and Electronics, 2022, 44(4): 1364-1371. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||