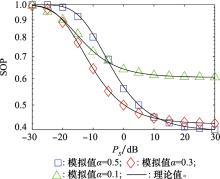
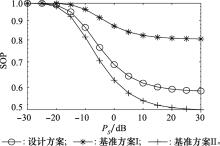
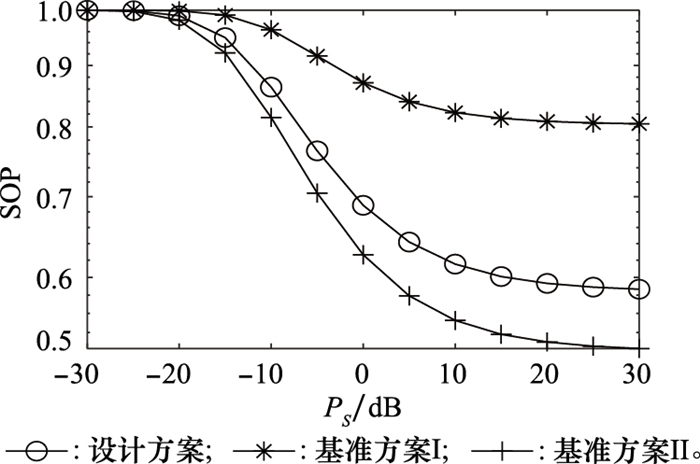
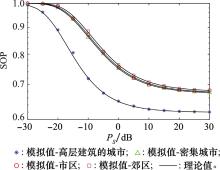
Systems Engineering and Electronics ›› 2022, Vol. 44 ›› Issue (1): 313-319.doi: 10.12305/j.issn.1001-506X.2022.01.39
• Communications and Networks • Previous Articles Next Articles
Secrecy performance analysis of UAV-based communications against full-duplex eavesdropping
Danyu DIAO1, Buhong WANG1,*, Kunrui CAO2, Runze DONG1, Tianhao CHENG1
- 1. School of Information and Navigation, Air Force Engineering University, Xi'an 710077, China
2. School of Information and Communications, National University of Defense Technology, Xi'an 710106, China
-
Received:2021-03-22Online:2022-01-01Published:2022-01-19 -
Contact:Buhong WANG
CLC Number:
Cite this article
Danyu DIAO, Buhong WANG, Kunrui CAO, Runze DONG, Tianhao CHENG. Secrecy performance analysis of UAV-based communications against full-duplex eavesdropping[J]. Systems Engineering and Electronics, 2022, 44(1): 313-319.
share this article
| 1 |
ZENG Y , ZHANG R , LIM T J . Wireless communications with unmanned aerial vehicles: opportunities and challenges[J]. IEEE Communications Magazine, 2016, 54 (5): 36- 42.
doi: 10.1109/MCOM.2016.7470933 |
| 2 |
LI B , FEI Z S , ZHANG Y , et al. Secure UAV communication networks over 5G[J]. IEEE Wireless Communications, 2019, 26 (5): 114- 120.
doi: 10.1109/MWC.2019.1800458 |
| 3 |
WANG H M , ZHANG X , JIANG J C . UAV-involved wireless physical-layer secure communications: overview and research directions[J]. IEEE Wireless Communications, 2019, 26 (5): 32- 39.
doi: 10.1109/MWC.001.1900045 |
| 4 | CHRYSIKOS T, DAGIUKLAS T, KOTSOPOULOS S, et al. Wireless information-theoretic security in MANETs[C]//Proc. of the IEEE International Conference on Communications Workshops, 2013. |
| 5 | LIU Y L , CHEN H H , WANG L M . Physical layer security for next generation wireless networks: theories, technologies, and challenges[J]. IEEE Communications Surveys & Tutorials, 2017, 19 (1): 347- 376. |
| 6 | HAMAMREH J M , FURQAN H M , ARSLAN H . Classifications and applications of physical layer security techniques for confidentiality: a comprehensive survey[J]. IEEE Communications Surveys & Tutorials, 2019, 21 (2): 1773- 1828. |
| 7 | MUKHERJEE A , FAKOORIAN S A A , HUANG J , et al. Principles of physical layer security in multiuser wireless networks: a survey[J]. IEEE Communications Surveys & Tuto-rials, 2014, 16 (3): 1550- 1573. |
| 8 |
ZHANG L , ZHAO H , HOU S , et al. A survey on 5G millimeter wave communications for UAV-assisted wireless networks[J]. IEEE Access, 2019, 7, 117460- 117504.
doi: 10.1109/ACCESS.2019.2929241 |
| 9 |
WYNER A D . The wire-tap channel[J]. Bell Labs Technical Journal, 1975, 54 (8): 1355- 1387.
doi: 10.1002/j.1538-7305.1975.tb02040.x |
| 10 | WU Q Q , ZENG Y , ZHANG R . Joint trajectory and communication design for multi-UAV enabled wireless networks[J]. IEEE Trans.on Wireless Communications, 2017, 17 (3): 2109- 2121. |
| 11 |
MA R Q , YANG W W , ZHANG Y , et al. Secure mmWave communication using UAV-enabled relay and cooperative jammer[J]. IEEE Access, 2019, 7, 119729- 119741.
doi: 10.1109/ACCESS.2019.2933231 |
| 12 | 张倩倩. 无人机协同传输通信系统物理层安全技术研究[J]. 信息技术与网络安全, 2020, 39 (5): 33- 36. |
| ZHANG Q Q . Research on physical layer security technology in UAV cooperative transmission communication system[J]. Network and Information Security, 2020, 39 (5): 33- 36. | |
| 13 |
JI B F , SONG K , LI C G , et al. Energy harvest and information transmission design in Internet-of-Things wireless communication systems[J]. AEU-International Journal of Electronics and Communications, 2018, 87, 124- 127.
doi: 10.1016/j.aeue.2018.01.038 |
| 14 | JI B F , LI Y Q , ZHOU B C , et al. Performance analysis of UAV relay assisted IoT communication network enhanced with energy harvesting[J]. IEEE Access, 2016, 4, 38738- 38747. |
| 15 |
ZENG Y , ZHANG R . Energy-efficient UAV communication with trajectory optimization[J]. IEEE Trans.on Wireless Communications, 2017, 16 (6): 3747- 3760.
doi: 10.1109/TWC.2017.2688328 |
| 16 |
YANG L , CHEN J C , HASAN M O , et al. Outage perfor-mance of UAV-assisted relaying systems with RF energy harvesting[J]. IEEE Communications Letters, 2018, 22 (12): 2471- 2474.
doi: 10.1109/LCOMM.2018.2876869 |
| 17 |
MAMAGHANI M T , HONG Y . On the performance of low-altitude UAV-enabled secure AF relaying with cooperative jamming and SWIPT[J]. IEEE Access, 2019, 7, 153060- 153073.
doi: 10.1109/ACCESS.2019.2948384 |
| 18 | XU J, ZENG Y, ZHANG R. UAV-enabled wireless power transfer: trajectory design and energy optimization[C]//Proc. of the IEEE 23rd Asia-Pacific Conference on Communications, 2017. |
| 19 | WU Q Q , LIU L , ZHANG R . Fundamental tradeoffs in communication and trajectory design for UAV-enabled wireless network[J]. IEEE Wireless Communications, 2019, 26 (1): 26- 44. |
| 20 | RIIHONEN T, KORPI D, RANTULA O, et al. On the prospects of full-duplex military radios[C]//Proc. of the IEEE International Conference on Military Communications & Information Systems, 2017. |
| 21 | HUANG W , CHEN W , BAI B , et al. Wiretap channel with full-duplex proactive eavesdropper: a game theoretic approach[J]. IEEE Trans.on Vehicular Technology, 2018, 67 (9): 7658- 7663. |
| 22 | JAYAKODY D N K, PERERA T D, NATHAN M C, et al. Self-energized full duplex UAV-assisted cooperative communication systems[C]//Proc. of the IEEE International Black Sea Conference on Communications and Networking, 2019. |
| 23 | LU H Q , DAI H B , SUN P , et al. Proactive eavesdropping in UAV-aided mobile relay systems[J]. EURASIP Journal on Wireless Communications and Networking, 2019, 68 (2): 1993- 1997. |
| 24 | WU W , WANG Y J , MO J L , et al. Robust proactive eavesdropping in UAV-enabled wireless communication networking[J]. EURASIP Journal on Wireless Communications and Network-ing, 2019, 285. |
| 25 |
LIU C X , LEE J , QUEK T Q S . Safeguarding UAV communications against full-duplex active eavesdropper[J]. IEEE Trans.on Wireless Communications, 2019, 18 (6): 2919- 2931.
doi: 10.1109/TWC.2019.2906177 |
| 26 |
RIIHONEN T , WERNER S , WICHMAN R . Mitigation of loopback self-interference in full-duplex MIMO relays[J]. IEEE Trans.on Signal Processing, 2011, 59 (12): 5983- 5993.
doi: 10.1109/TSP.2011.2164910 |
| 27 |
KORPI D , TAMMINEN J , TURUNEN M , et al. Full-duplex mobile device-pushing the limits[J]. IEEE Communications Magazine, 2016, 54 (9): 80- 87.
doi: 10.1109/MCOM.2016.7565192 |
| 28 |
DUARTE M , DICK C , SABHARWAL A . Experiment-driven characterization of full-duplex wireless systems[J]. IEEE Trans.on Wireless Communications, 2012, 11 (12): 4296- 4307.
doi: 10.1109/TWC.2012.102612.111278 |
| 29 | MILTON A . Handbook of mathematical functions with formulas, graphs, and mathematical tables[J]. American Journal of Physics, 1988, 56 (10): 958. |
| 30 | ZHOU Y, YEOH P L, CHEN H, et al. Secrecy outage probability and jamming coverage of UAV-enabled friendly jammer[C]//Proc. of the 11th International Conference on Signal Processing and Communication Systems, 2017. |
| [1] | Xueyong YU, Ye ZHU, Lixiang QIU, Hongbo ZHU. Energy efficient offloading strategy for UAV aided edgecomputing systems [J]. Systems Engineering and Electronics, 2022, 44(3): 1022-1029. |
| [2] | Xiaorong JING, Zhenyuan SONG, Yue LUO, Yudan MA. Design of physical layer safety scheme aided with IRS and artificial noise for MIMO communication systems [J]. Systems Engineering and Electronics, 2022, 44(10): 3266-3274. |
| [3] | Bing FANG, Bing HAN. Secure beamforming method for the MISO SWIPT system [J]. Systems Engineering and Electronics, 2021, 43(6): 1692-1698. |
| [4] | Chenwei GU, Zhi LIN, Min LIN, Luyao XIE, Jian OUYANG, Shuo HUANG. Robust secure beamforming design for the downlink of satellite communications [J]. Systems Engineering and Electronics, 2021, 43(5): 1361-1370. |
| [5] | Chonglin HE, Ziwen SUN. Multi-level Stackelberg game model against full-duplex attacking node in IWSN physical layer [J]. Systems Engineering and Electronics, 2021, 43(10): 2931-2939. |
| [6] | Weijia LEI, Yuyu LI. Double scrambling scheme for reducing security gap of channel codes [J]. Systems Engineering and Electronics, 2020, 42(2): 458-465. |
| [7] | ZHU Jiang, WANG Zhihao. TRAN-SWIPT energy efficiency secure transmission scheme based on Lyapulov optimization [J]. Systems Engineering and Electronics, 2019, 41(12): 2879-2884. |
| [8] | FU Xiaomei, CHEN Li, CHANG Shuai. Prediction of untrusted relay behavior based on physical layer security features [J]. Systems Engineering and Electronics, 2018, 40(3): 671-675. |
| [9] | . Synthesis algorithm of directional modulation signals based on sparse arrays [J]. Systems Engineering and Electronics, 2018, 40(12): 2816-2823. |
| [10] | LEI Weijia, YANG Xiaoyan, LIN Xiuzhen. Secure transmission scheme based on SWIPT relay with antenna grouping [J]. Systems Engineering and Electronics, 2017, 39(8): 1849-1856. |
| [11] | FU Xiao-mei, YAO Xiao-ming, ZONG Qun. Relay selection and power optimization in cooperative coalitions [J]. Systems Engineering and Electronics, 2016, 38(5): 1176-. |
| [12] | ZHANG Shunwai1, YANG Fengfan2, SONG Rongfang1. Performance analysis and codes design of coded#br# cooperation with energy harvesting [J]. Systems Engineering and Electronics, 2016, 38(12): 2863-2868. |
| [13] | WANG Shu, DA Xin-yu, CHU Zhen-yong. Wiretapping strategies for artificial noise assisted communication in MU-MIMO system [J]. Systems Engineering and Electronics, 2016, 38(11): 2648-2652. |
| [14] | HONG Tao, LI Zhi-peng. Research of the peak-to-average power ratio problem for physical-layer security communication system aided by artificial noise [J]. Systems Engineering and Electronics, 2016, 38(11): 2653-2659. |
| [15] | LEI Wei-jia, JIANG Xue, ZUO Li-jie, XIE Xian-zhong. Secrecy rate optimization for two-hop relay system with energy#br# harvesting based on cooperative jamming [J]. Systems Engineering and Electronics, 2015, 37(12): 2835-2841. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||